What is Email Spoofing?
According to Forbes magazine, scammers send 3.1 billion domain spoofing emails every day. Moreover, to carry out these email scams, cyber criminals impersonate a company, an organisation, or a friend to trick users. The motive behind these scams is to convince users to divulge sensitive information, login credentials or financial information. This fraud strategy of creating a forged sender address to dupe recipients is called email spoofing.
Shockingly, email spoofing is not restricted to impersonating the second person or third person. There are many instances where hackers impersonate the user themselves.
To clarify, email spoofing is the fraudulent act of creating a forged email header to trick the recipient into thinking that the email has originated from a known or legitimate source. Today, phishing emails and business email compromise (BEC) scams are evolving at a rapid rate due to email spoofing. In fact, email spoofing has been responsible for many well publicised email-based security incidents, ultimately resulting in serious financial loss and damage to reputations.
Current Statistics on Email Spoofing Scams
- According to Forbes, scammers send 3.1 billion domain spoofing emails per day.
- From over 300 billion emails sent every day, 3-6 billion email scams are attempted daily.
- Reportedly, business email compromises have risen by 100%. – WRAL TechWire
- Phishing scammers actively have impersonated some of large institutions like the World Health Organisation (WHO) and various government departments to capitalise on Covid-19 fears.
- According to the FBI, in the USA, business email compromises (BECs) have cost companies more than $26 billion between 2016 and 2019.
- According to the MediaPost cyber security survey, while 51% of companies were affected by the ransomware attack, 60% of the companies witnessed an increase in email-based impersonation fraud.
- MediaPost also reported that email attacks increased by 30% in the first 100 days of the pandemic this year.
How to Stop Email Spoofing Attacks?
The email security report of 2020 states that domain spoofing and email spoofing are currently the main attack vectors today. Moreover, it has been reported that there will be an expected increase in email spoofing within the next 12 months. But what empowers these cyber frauds to attempt email-based attacks? The most common and possible reason is typically a lack of email authentication.
The Simple Mail Transfer Protocol (SMTP) doesn’t provide any mechanism for authentication of email addresses. Taking advantage of this vulnerability, cyber frauds alter different email sections to impersonate as a legitimate sender identity.
To prevent email spoofing attacks, various email authentication protocols and standards have been developed, the following are certainly worth considering implementing of you haven’t done so already.
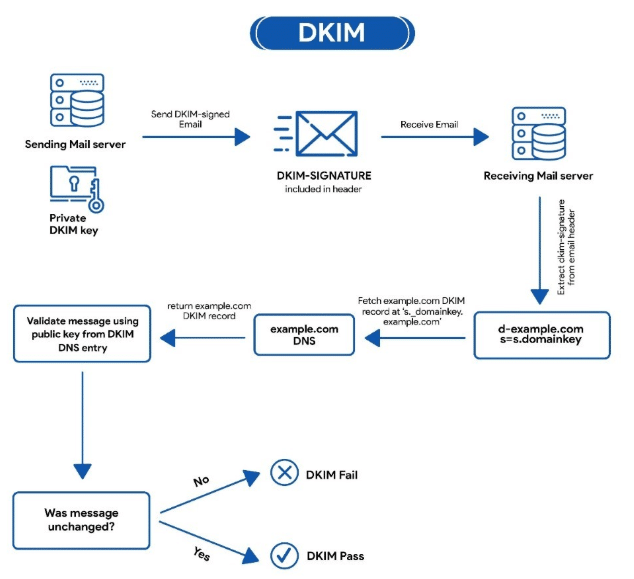
DMARC (Domain-based Message Authentication Reporting and Conformance)
An email authentication protocol that gives the sender the option of letting the recipient know if the email is protected by DKIM or SPF. It is designed and developed to empower domain owners in protecting their domain from unauthorised or malicious use such as email spoofing. Primarily, implementing DMARC helps in securing domains from email-based attacks like BEC attacks, email and phishing attacks.
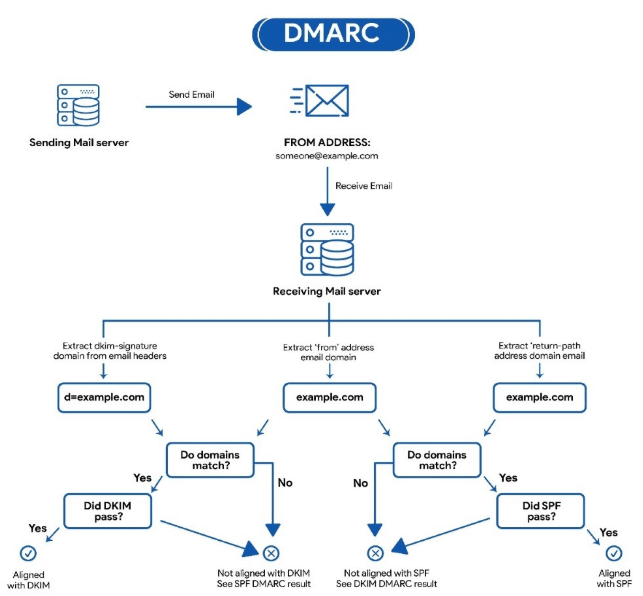
SPF (Sender Policy Framework)
An email authentication standard that detects forged sender addresses while the email is being delivered to the recipient. The SPF allows the receiving email server to check during email delivery whether the email that claims to have come from a particular domain is from a valid IP address enlisted in the domain record or not. The list of authorised IP addresses and sending hosts for a specific domain is published in the DNS records for that domain. The SPF record provides an extra layer of stringent protection when implemented in conjunction with DMARC and DKIM. It outlines the authentic IP addresses that are authorised to send emails to a particular domain.
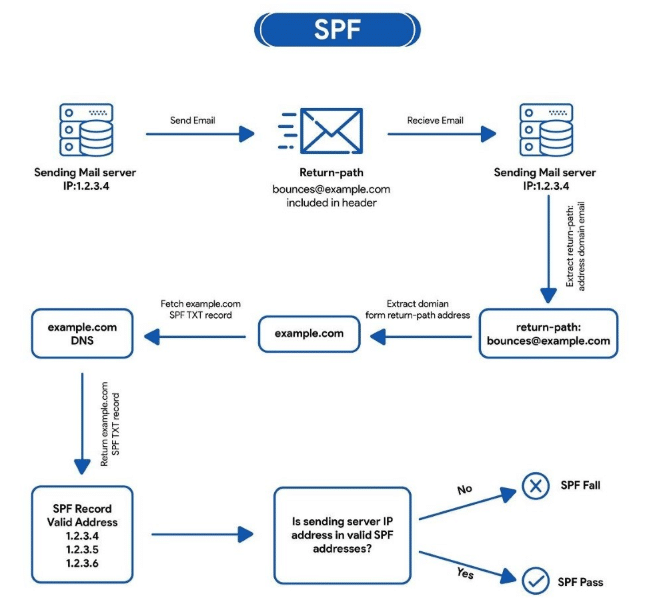
DKIM (Domain Key Identified Mail)
This email authentication standard uses a pair of cryptographic keys to sign outgoing emails to ensure that email is not altered from when it was sent. It allows the recipient to check if the email that claims to have come from a particular domain is actually authorised by the domain’s owner or not. Here the digital signature is added to the headers of the email message. This standard allows the sender to establish trust by providing security against spoofing of an email in which the outbound emails are sent on behalf of the user’s domain.
On implementing these email authentication protocols, an organisation can not only enhance the email deliverability rate but also, ensure the security of outbound emails against email spoofing scams.
Apart from these email authentication protocols and standards, organisations should also ensure that their employees are aware of the prevailing cyber threats. They should be provided with a robust security awareness training in which they are educated on how to recognise and combat all types of cyber threats in order to mitigate cyber risks to the organisation.
Also, due to the pandemic, many organisations have embraced remote working, and this calls for a resilient cyber security working environment. Therefore, now, more than ever it is so important that security leaders in every organisation should invest in the best practice for cyber security, layering training, awareness and technology to mitigate risk and protect the business, its reputation, its information assets and its staff from cyber harm.
To find out how we can support you on your journey to secure email communications, please call us on 0191 562 3228 or visit our Zivver page.